Important AppVeyor Server 7.0.2915 update
Posted on August 18, 2020
A vulnerability was found in self-hosted AppVeyor Server 7.0.2546 for Linux.
We encourage all users of self-hosted AppVeyor Server to upgrade their installations to the latest AppVeyor Server 7.0.2915 as soon as possible.
Follow this guide to upgrade your AppVeyor Server installation to the latest version. Before performing any upgrade please make sure to backup your current installation of AppVeyor Server!
Vulnerability details are scheduled to be published on August 25th.
Best regards,
AppVeyor team
Global YAML - configure actions and variables for all projects
Posted on May 07, 2020
AppVeyor customers have been asking about an ability to configure environment variables that are common for all projects under account. These could be a secure variable with SSH key for accessing the repo, a password for signing certificate or some other value you don’t want to include into every project’s appveyor.yml.
We’ve finally got a solution for that! Global YAML is a configuration in appveyor.yml format which is “injected” into all projects under the account. It can be edited on Account → Global YAML page. The idea of using the same appveyor.yml syntax for global configuration worked so good and natural that it gone beyond just environment variables - you can “globalize” pretty much everything:
- Clone script overriding built-in cloning commands;
- Environment variables,
/etc/hostsandcacheentries; init,installactions;- Before/after scripts for build, test and deploy phases;
- Artifacts;
- Deployment steps;
- Notifications;
- Build finalizers:
on_success,on_failureandon_finish.
Consider this global configuration for example:
environment:
MY_SECRET_ACCOUNT:
secure: AAAAABBBBEEEEE22==
MY_SECRET_KEY:
secure: AABBCC11==
init:
- ps: gcim Win32_Processor | % { "$($_.NumberOfLogicalProcessors) logical CPUs" }
- ps: gcim Win32_OperatingSystem | % { "$([int]($_.TotalVisibleMemorySize/1mb)) Gb" }
notifications:
- provider: Slack
incoming_webhook:
secure: AAABBB+CCC+DDD==
channel: '#ci'
on_build_failure: true
The configuration above defines two secure variables MY_SECRET_ACCOUNT and MY_SECRET_KEY that will be available in all builds under your account, outputs VM configuration (you can display any instrumental data relevant to your projects) in the beginning of each build and, finally, sends notification to a Slack channel on every build’s failure.
Read more about what sections are supported and how they are merged into the projects.
Enjoy!
Introducing job workflows - sequential flows, fan-in, fan-out and cancellable jobs
Posted on March 23, 2020
AppVeyor can run “matrix” builds where you specify “dimensions” like image, platform, configuration, etc. and AppVeyor creates a build with multiple jobs testing all combinations of configured dimensions. All matrix build jobs are running in parallel (provided your account allows multiple concurrent jobs).
However, there could be more advanced CI/CD workflow requirements that cannot be implemented in a single build job or parallel matrix, for example:
- Building the project/tests once and then run multiple tests in parallel for the same build output;
- Deploy once all tests running in parallel are finished;
- Deploy to staging, run tests on staging, deploy to production, run tests on production.
AppVeyor allows to configure explicit jobs and their groups with dependencies between them which enables developer to run build jobs in sequence, implement fan-out/fan-in pipelines and spawn independent cancellable jobs.
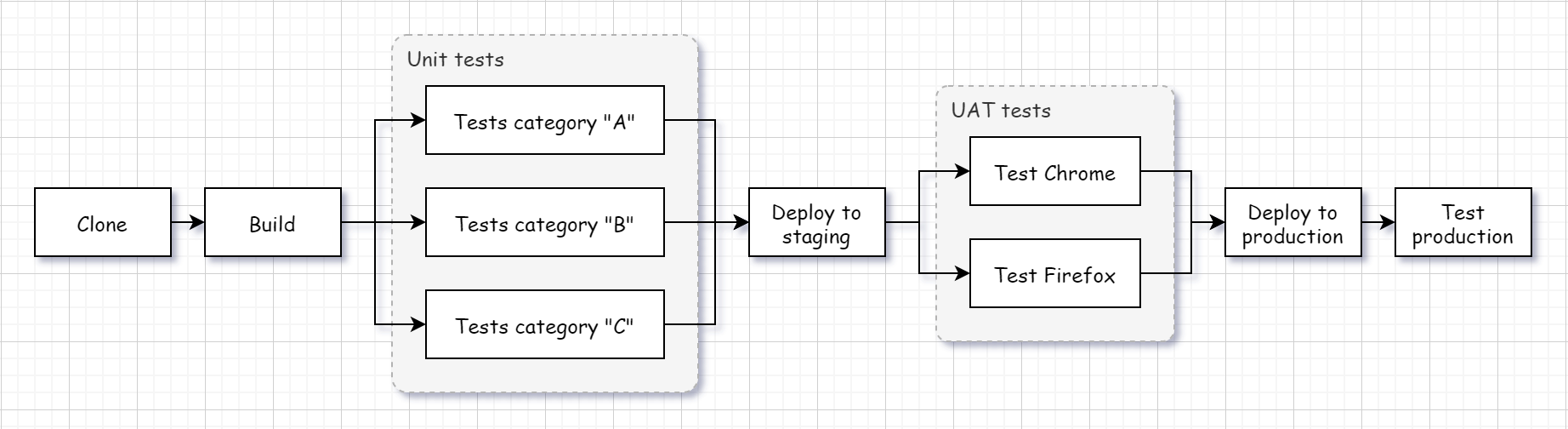
Configuring job workflows
A general template for defining job workflows in appveyor.yml:
# Job definitions, sections in [] are optional
environment:
matrix:
- job_name: <job name 1>
[- job_group: <group name>]
[- jobs_per_group: N]
[- job_depends_on: <job or group name>]
[- job_allow_cancellation: true]
- job_name: <job name 2>
[- job_group: <group name>]
[- jobs_per_group: N]
[- job_depends_on: <job or group name>]
[- job_allow_cancellation: true]
...
# the first failed job cancels other jobs and fails entire build
matrix:
fast_finish: true
# configuration common for all jobs
init:
- appveyor version
- echo Some common logic here...
# job-specific configurations
for:
-
matrix:
only:
- job_name: <job name 1>
[- job_group: <job name 1>] # optionally, you can define the configuration for the entire group
build_script:
- echo Job 1
-
matrix:
only:
- job_name: <job name 2>
build_script:
- echo Job 2
...
The following example creates a build with 2 jobs building solution in parallel on Windows and Linux images:
environment:
matrix:
- job_name: Windows build
appveyor_build_worker_image: Visual Studio 2019
- job_name: Linux build
appveyor_build_worker_image: Ubuntu
matrix:
fast_finish: true
init:
- appveyor version
# job-specific configurations
for:
-
matrix:
only:
- job_name: Windows build
build_script:
- cmd: echo This is Windows-specific build script
-
matrix:
only:
- job_name: Linux build
build_script:
- sh: echo This is Linux-specific build script
Sequential flow
Build can be configured to run jobs one-by-one, for example build solution, deploy to staging, run tests on staging, deploy to production, run tests on production.
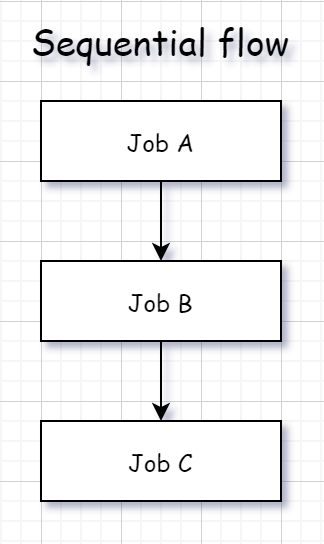
We use job_depends_on to implement sequential flow:
environment:
matrix:
- job_name: Job A
- job_name: Job B
job_depends_on: Job A
- job_name: Job C
job_depends_on: Job B
...
Fan-in, fan-out
Fan-out flow is when multiple jobs are spawned in parallel once a single job or a group is completed. Fan-in flow is when a single job or a group waits for a multiple jobs to complete:
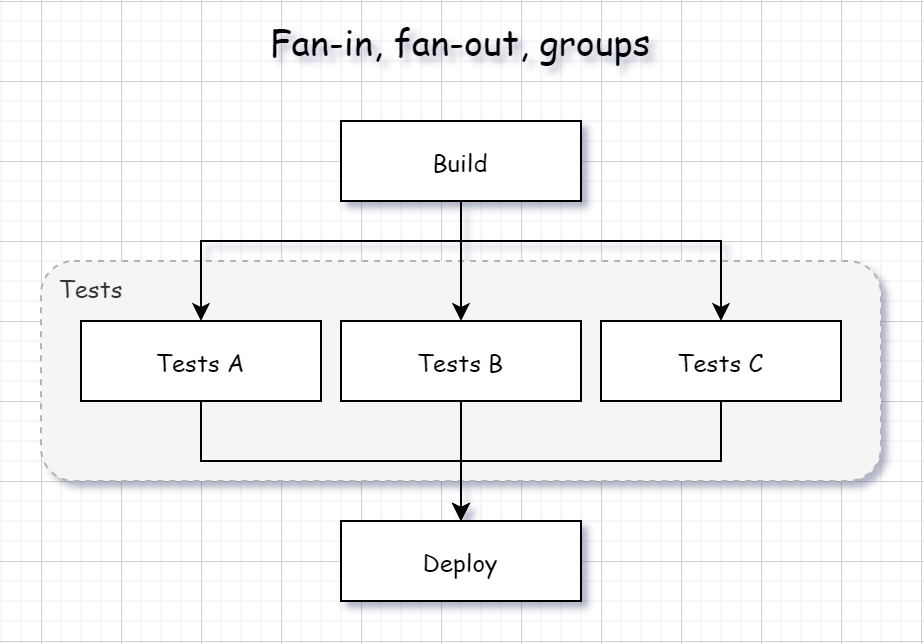
The is appveyor.yml for the scenario presented on the figure above:
environment:
matrix:
- job_name: Build
- job_name: Tests A
job_group: Tests
job_depends_on: Build
- job_name: Tests B
job_group: Tests
job_depends_on: Build
- job_name: Tests C
job_group: Tests
job_depends_on: Build
- job_name: Deploy
job_depends_on: Tests
...
Cancellable jobs
You can have jobs which are automatically cancelled when the entire build is complete (succeeded or failed - doesn’t matter). These jobs could be some sort of “monitors” or services/dependencies (such as container with Redis or database) in Docker builds.
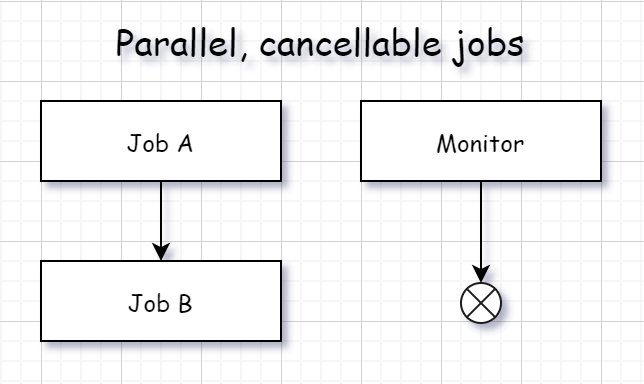
An example of cancellable job doing some work in a loop while the build is working:
environment:
matrix:
- job_name: Main work
- job_name: Monitor
job_allow_cancellation: true
for:
-
matrix:
only:
- job_name: Main work
build_script:
- cmd: echo This is the main job
-
matrix:
only:
- job_name: Monitor
build_script:
- ps: while($true) { Write-Host 'Do some checks'; Start-Sleep -s 1; }
Customizable build images and faster builds with AppVeyor
Posted on February 06, 2020
Hosted CI/CD service is all about the right software provided on the base images. We are continuously working on upgrading images with the latest software releases and security updates making sure you are on the cutting edge of technology. It works great for most of the teams, but not for all.
If you had ever found the images are updated too fast or too slow or you need some specific software on them, now we’ve got a solution for you!
Customizable images
With customizable images you can install your own software and build dependencies on top of AppVeyor-provided base images (Windows, Linux) and then use the resulting image for further builds.
Custom images enable new use cases that were not possible before in a hosted CI/CD:
- update image software at your own pace - pin specific versions or be on a cutting edge;
- speed up builds drastically by preserving VM state between builds - next-gen build cache;
- securely store certificates and other secrets within the image;
- migrate on-premise CI workflows with proprietary, licensed, manually-installed, legacy software to a hosted CI.
Check this guide to see how easy it is to build your custom image!
Faster builds
Not only customizable images can speed up your builds. You can now run your builds in a personalized cloud environment with more powerful VMs than in our own in-house cloud.
Out tests show that by using “Medium” instances on Google Cloud you can get 2-3 times faster builds!
Request your trial for custom images and faster VMs now.
Best regards,
AppVeyor team
Build macOS projects with AppVeyor
Posted on November 20, 2019
Today we are adding macOS to our hosted CI/CD environment. Now you can consolidate all your multi-platform projects and run Windows, Linux and macOS builds with AppVeyor.
As with our Windows and Linux environments, we are committed to provide you with the most recent software and complete toolset for macOS. You can choose from two macOS images:
macos- macOS 10.15 “Catalina”macos-mojave- macOS 10.14 “Mojave”
Both images have the latest XCode 11.2.1 pre-installed, all the latest versions of Node.js, Go, Java, .NET Core, Ruby, Python and compilers. You can find the full list of pre-installed software on this page.
macOS builds are available to everyone by request - send us an email.
Best regards,
AppVeyor team